Ubisoft UPlay has serious security vulnerability
Update: New patch plugs the leak.
UPDATE:
Ubisoft has rolled out a 2.0.4 patch which appears to kill the vulnerability found in UPlay. The changelog for the patch says: "Fix addressing browser plug-in. Plug-in now only able to open UPlay application". We have tested the new update and confirm that the issue appears to have been resolved. If you own any game with UPlay support, we recommend running the client and allowing it to update in order to close the loophole.
ORIGINAL STORY:
Ubisoft's UPlay client appears to host a serious security vulnerability that could allow malicious websites to take control of your PC, according to programmer Tavis Ormandy, posting on the SecLists.Org's "full disclosure" mailing list. The vulnerability affects anyone with key Ubisoft games installed, including several Assassin's Creed releases (AC2 to Revelations), HAWX 2, Splinter Cell: Conviction and Ghost Recon: Future Soldier.
"While on vacation recently I bought a video game called 'Assassin's Creed Revelations'. I didn't have much of a chance to play it, but it seems fun so far. However, I noticed the installation procedure creates a browser plugin for its accompanying UPlay launcher, which grants unexpectedly (at least to me) wide access to websites," Ormandy notes.
"I don't know if it's by design, but I thought I'd mention it here in case someone else wants to look into it (I'm not really interested in video game security, I air-gap the machine I use to play games)."
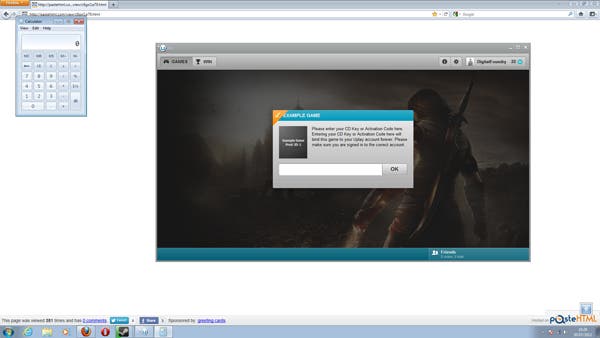
Ormandy also supplied a proof of concept demonstrating the security hole. Accessing a specific website set-up with his code sees UPlay booted, and the standard Windows calculator program then runs completely independently of user input. We tested it by accessing the link after installing Assassin's Creed 2, and updating UPlay to the latest version. Suffice to say that browser-based scripts should not be able to run any kind of executable code outside of the browser, but that's exactly what happens.
The implications here are cause for concern: the exploit could be used to install trojans or other rogue software on your PC. Scripts could be set-up that would wipe any data on your PC where the user has access. It's highly unlikely that Ubisoft left this backdoor in here on purpose, but regardless, it appears to have all the hallmarks of a major oversight that the firm should be correcting as a matter of extreme urgency.
Also, accusations have been levelled that UPlay is a "root kit", suggesting that it is something that hides itself by hijacking essential system tools and prevents them from showing the attacker's files. We've found nothing to suggest that UPlay has any kind of malicious intent along those lines, and while it looks like a highly significant lapse in security we don't think it can provide hackers with root access to your PC. Windows UAC should kick in whenever any such attempts are made.
So, how to protect yourself? Anyone with a PC title installed using the UPlay system can prevent the exploit from working by disabling the UPlay browser plug-in - in theory, it's as simple as that. Stopping the browser from running the plug-in closes the backdoor, and without that crucial bridge, malicious HTML based on this exploit will not function.
Ubisoft had no comment for Eurogamer when approached about the matter.