Hackers leave PS3 security in tatters
Linux returns and widespread piracy could follow.
PlayStation 3's internal security scheme is a shambles, with all of its major anti-piracy features failing abysmally. The system is so vulnerable that hackers now have the exact same privileges as Sony in deciding what code can run on the console.
So says the self-styled "Fail0verflow" team, hackers with a successful track record in opening up closed devices such as the Nintendo Wii for running homebrew code and – of course – perennial favourite, Linux. Yes, despite the removal of OtherOS, Linux is coming back to PS3.
Fail0verflow's comments, presented at the 27th Chaos Communication Conference (27c3) might seem somewhat at odds with reality. PlayStation 3 launched in NTSC territories in November 2006 and yet the first widespread piracy only kicked in this summer with the release of PSJailbreak.
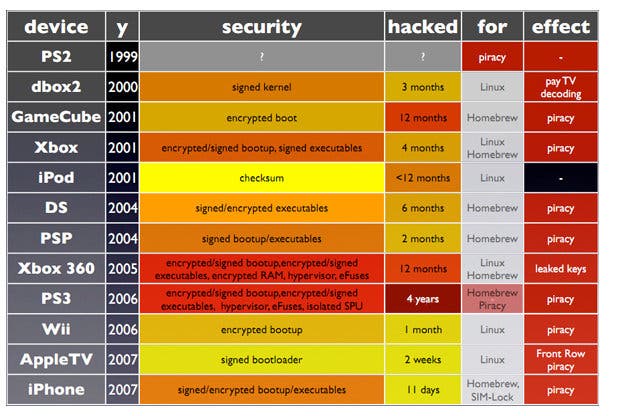
IBM's Cell Broadband Engine has been widely praised for its tough on-die security features which ensure that none of the essential decryption keys ever leave the main CPU, and so can't be accessed via RAM dumps. The protection has certainly lasted longer than that of the Wii and Xbox 360, both of which have been running pirate games for years now.
Fail0verflow's explanation? Hackers want to run their own code on the hardware they buy and PS3 allowed them to do that from day one. Only when the Linux-stripped PS3 Slim appeared – which they say can run the OS just as well at the older model – and when OtherOS was removed from the "fat" console, were the hackers suitably motivated to expose the security shortcomings of the system.
The team also believe that piracy is a consequential effect of such hacks, and that the PS3 remained secure for as long as it did simply because hackers weren't interested in opening up a system that was already open enough, with Linux implementations supported vigorously at launch by the platform holder.
Across a 45-minute presentation, the team revealed the methodology that made the on-die security an irrelevance and proved beyond doubt that the Hypervisor tech – the CPU guardian that is supposed to stop unauthorised code running – was almost completely pointless.
According to the Fail0verflow team, the PS3's architecture appears to allow the execution of rogue "unsigned" code with only the minimum of effort required from a determined hacker – which seems to explain in part how the PSJailbreak exploit was able to run pirate games even though the Hypervisor was not touched at all.
Based on their presentation, it looks as though the team has not cracked the Hypervisor even with the new hack, but their contention is that its application is an irrelevance anyway. Even specific code that Sony revokes and bans from use within the PS3 isn't actually being checked when it is run, so after the Hypervisor's cursory check, rogue code can be patched back in and run as per normal.
However, the Fail0verflow team's work goes way beyond this traditional style of hacking. They have released the technique by which any kind of unauthorised code can be run on any PS3. Every PS3 executable file is encrypted, or signed, using private ciphers only available (in theory) to Sony itself. It has long been established that brute-forcing the keys would take hundreds of thousands of computers hundreds of thousands of years to complete.
However, despite this mathematical reality, Fail0verflow are now in possession of all of the encryption keys Sony uses. They can create DLC-style packages that will run on any PlayStation 3, and yes, they can create their own custom firmware upgrades. Their stated aim is to produce their own firmware update that boots directly into Linux on any PS3, but the methodology allows for any kind of custom firmware to be produced – and we all know what that means.
So how did Fail0verflow get the keys so quickly? Well, in creating the encrypted files, an important element of the mathematical formula is the use of a random number. The PS3 encryption scheme uses just a single random number that never varies between each signed file, while the proper way of carrying out the signing process is to use a different random number every time a file is signed. Armed with just two signatures, it is possible to mathematically reconstruct the encryption key thanks to this constant variable. In theory, it's as simple as that. In practice, some simple equation work is required.
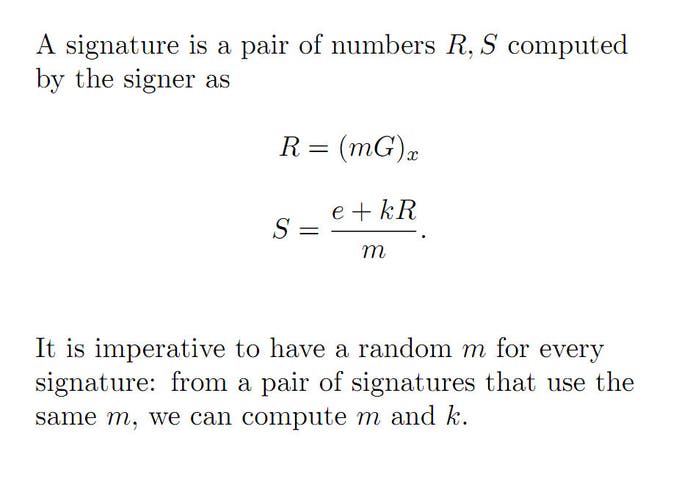

There are many different keys used by Sony – keys for game code, firmware components, and the isolated SPU decryption system, for example. All of them have been encrypted with the same random number faux pas, meaning that all of them can be reversed. In a stroke, hackers now have the exact same privilege level for running code as Sony itself, and this encompasses all file-types the console uses.
It's a monumental error made by the platform holder that has serious repercussions for the future of the PlayStation 3. Hardware hacks like flashed Xbox 360 DVD drives and modchipped Wiis seem to introduce an inherent limitation that stops a majority of devices from being modified: maybe people just don't have the skill or the willingness to toss away their warranties. But a full software hack like this one, compatible with all machines currently on the market, can spread like wildfire.

